Watch Out for Fake Microsoft Patches
I just finished dealing with an incident as a result of a user clicking on an email asking him to install a Microsoft Patch. Instead of fixing his PC (which was fixed anyway because our patch management RULEZ!!1!) he downloaded a trojan that started flooding spam.
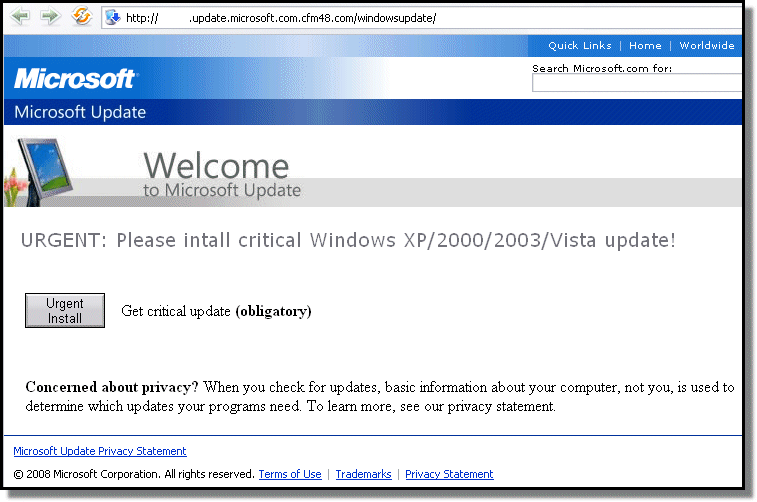
FSecure has a great screenshot of it here, along with a demonstration of how the domain name that is hosting the patch is actually a distributed beastie and has the ability to constantly mutate to avoid being shutdown. FSecure calls it a “fast flux” domain.
You can’t just block a single IP with a router. This type of block should be put in three places. First, put a block in the gateway Antivirus system to stop all emails containing the domain in the body text pertaining to the fast flux domain. Next, blacklist the DNS of the domain if you have an internal DNS system. Finally, put a block for that url in your content filters to prevent your users from surfing to that domain in case the local hosts file is compromised.
So what are you waiting for? Block cfm48.com now.

I love it when I run across one of these while I’m running LINUX!!!
Not only that, Microsoft doesn’t email patches to anyone. And the only people more pretentious than Apple snobs are Linux snobs. 😉
I dual boot actually. Linux for home. Windows for work. 8)
I just got a 400GB hard drive. I might get me a nice Linux flavor to play with. Which one do you use?
Linux Mint. It’s an offshoot of Ubuntu. very little fuss.